Manage Security Profiles
Manage Security Profiles allows the security engineer to create, updated, and destroy security profiles in the system. Security profiles are attached to identity elements in the system and enforce security policies contained in the profiles.
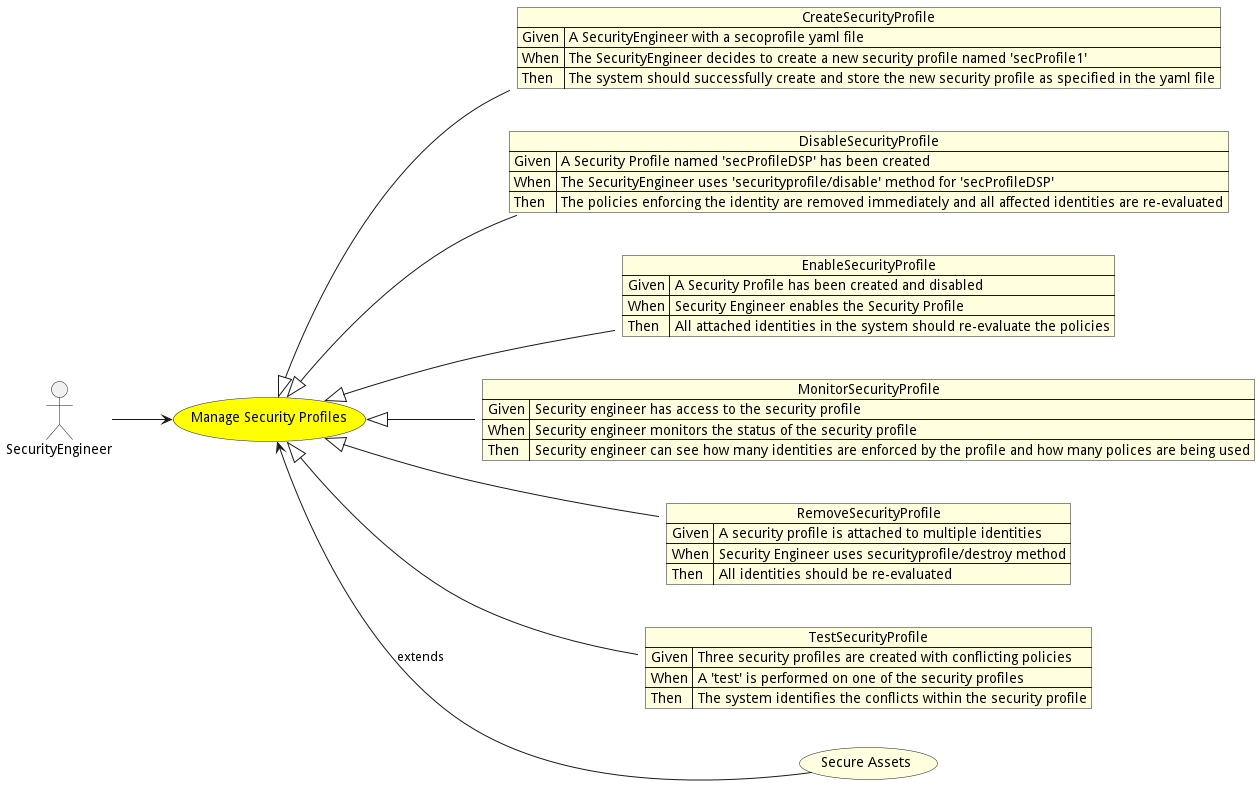
Actors
Extends Use Cases
Detail Scenarios
- CreateSecurityProfile
- DisableSecurityProfile
- EnableSecurityProfile
- MonitorSecurityProfile
- RemoveSecurityProfile
- TestSecurityProfile
Scenario Create Security Profile
Create Security Profile from a secoprofile yaml file.
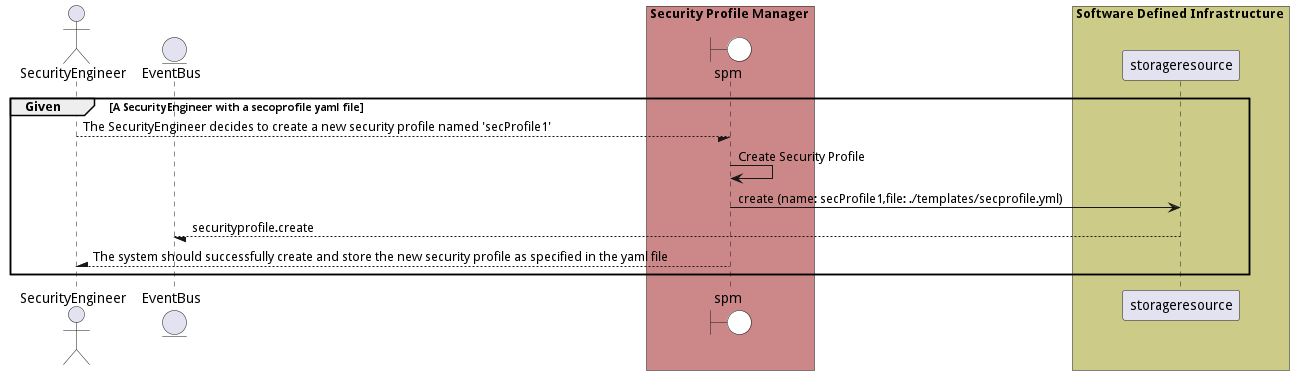
Criteria
- Given - A SecurityEngineer with a secoprofile yaml file
- When - The SecurityEngineer decides to create a new security profile named 'secProfile1'
- Then - A SecurityEngineer with a secoprofile yaml file
Steps
Actors
Scenario Disable Security Profile
Disable Security Profile that has been created. This should remove the policies enforcing the identity immediately. All identities effected should be re-evaluated.
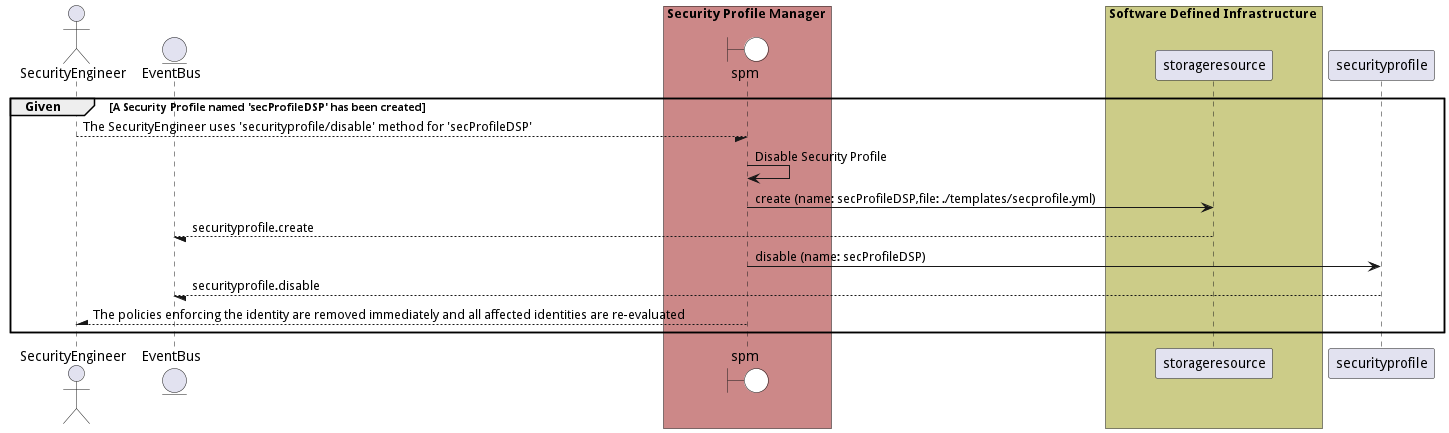
Criteria
- Given - A Security Profile named 'secProfileDSP' has been created
- When - The SecurityEngineer uses 'securityprofile/disable' method for 'secProfileDSP'
- Then - A Security Profile named 'secProfileDSP' has been created
Steps
- securityprofile create –name secProfileDSP –file ./templates/secprofile.yml
- securityprofile disable –name secProfileDSP
Actors
Scenario Enable Security Profile
Enable Security Profile should force a re-evaluation of the policies on all of the attached identities in the system.
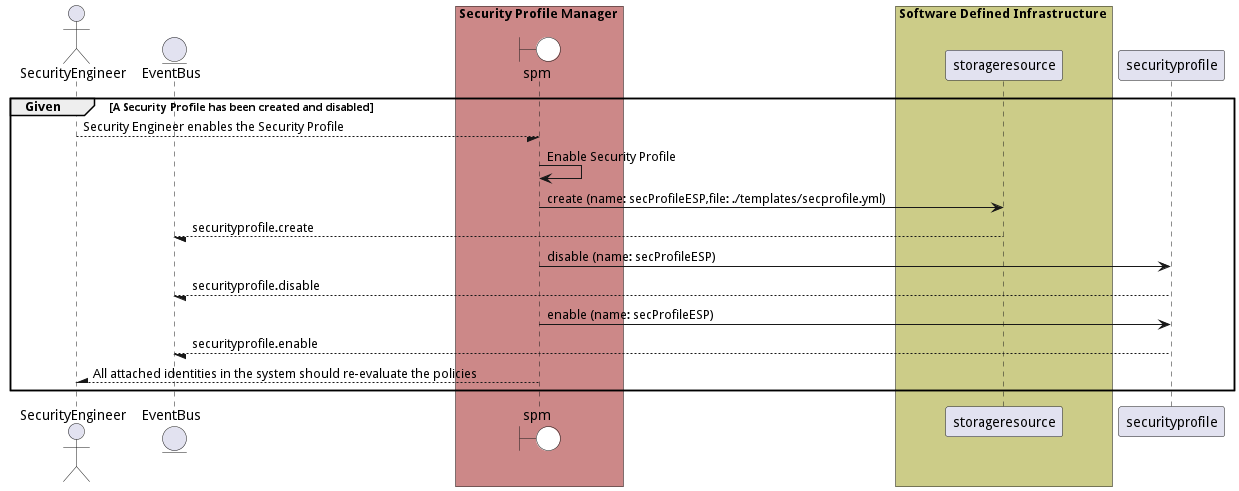
Criteria
- Given - A Security Profile has been created and disabled
- When - Security Engineer enables the Security Profile
- Then - A Security Profile has been created and disabled
Steps
- securityprofile create –name secProfileESP –file ./templates/secprofile.yml
- securityprofile disable –name secProfileESP
- securityprofile enable –name secProfileESP
Actors
Scenario Monitor Security Profile
Monitor Security Profile allows the security engineer to monitor the status of the security profile. Including how many identities are enforced by the profile and how many polices are being used.
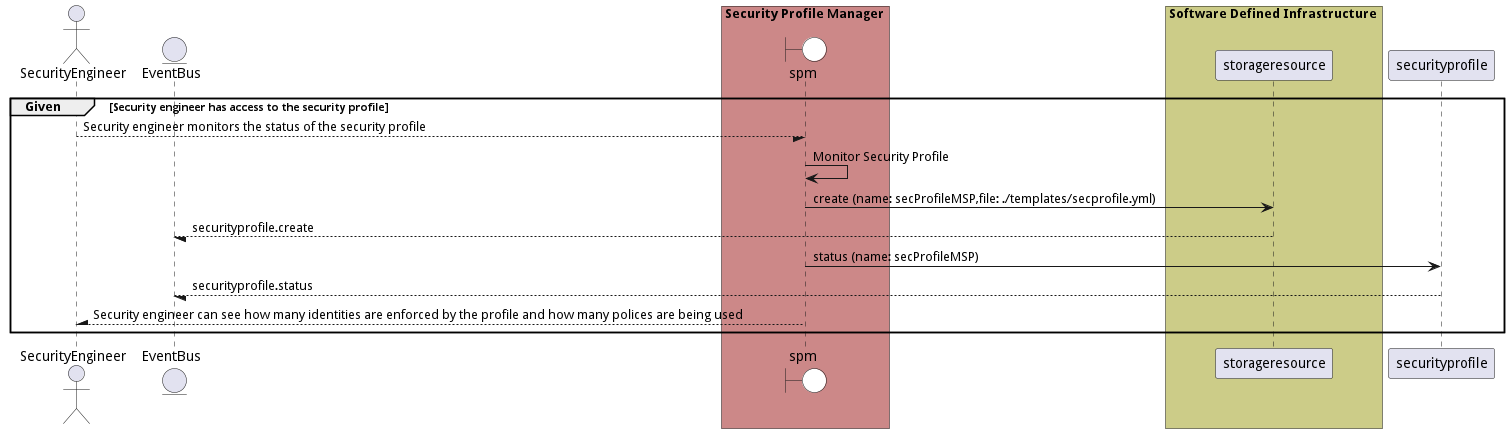
Criteria
- Given - Security engineer has access to the security profile
- When - Security engineer monitors the status of the security profile
- Then - Security engineer has access to the security profile
Steps
- securityprofile create –name secProfileMSP –file ./templates/secprofile.yml
- securityprofile status –name secProfileMSP
Actors
Scenario Remove Security Profile
Remove Security Profile that is attached to multiple identities. All identities should be re-evaluated when a profile is destroyed.
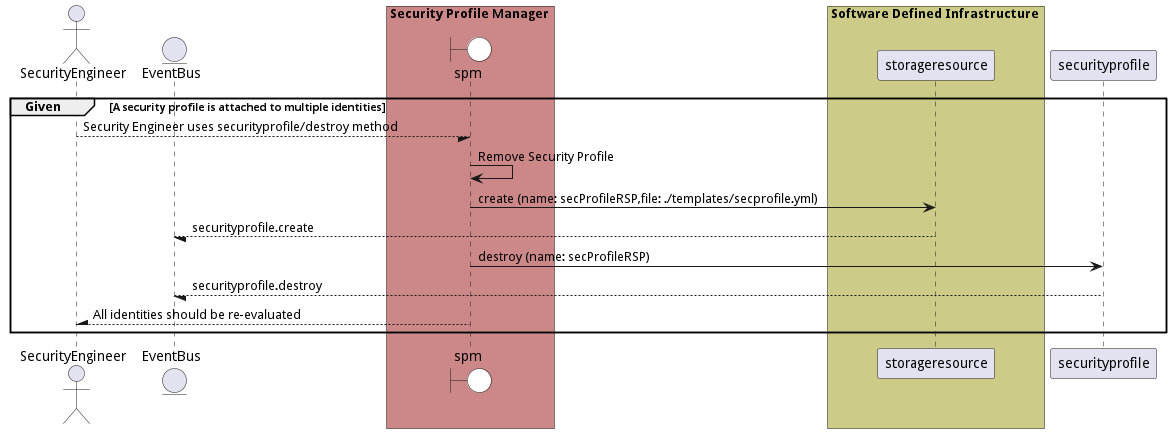
Criteria
- Given - A security profile is attached to multiple identities
- When - Security Engineer uses securityprofile/destroy method
- Then - A security profile is attached to multiple identities
Steps
- securityprofile create –name secProfileRSP –file ./templates/secprofile.yml
- securityprofile destroy –name secProfileRSP
Actors
Scenario Test Security Profile
Test Security Profile if the profile has conflicting policies and if the profile conflicts with other profiles in the system and when it is attached.
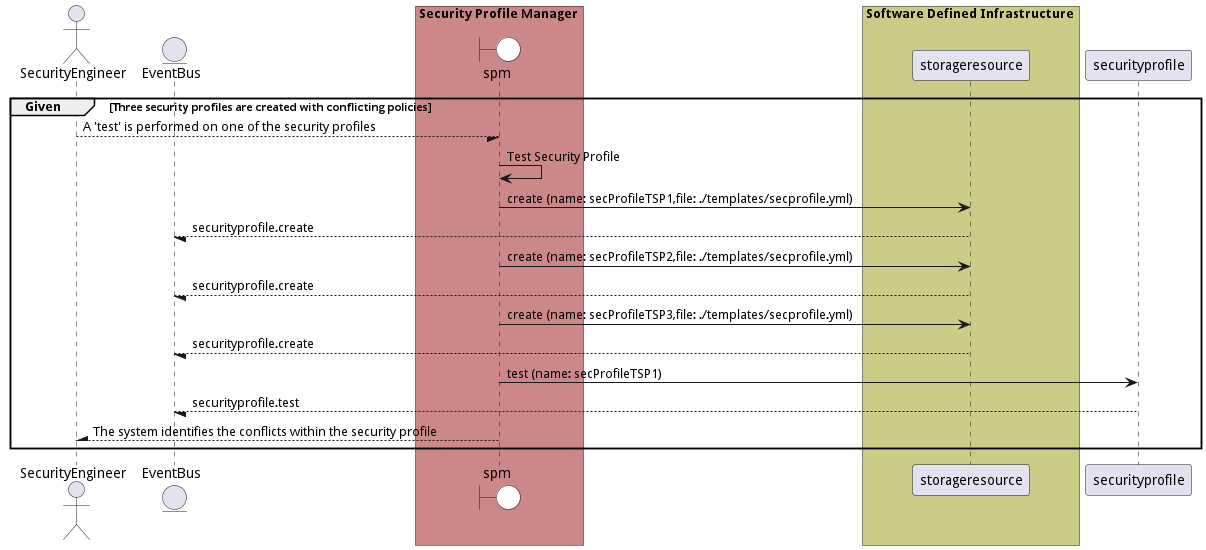
Criteria
- Given - Three security profiles are created with conflicting policies
- When - A 'test' is performed on one of the security profiles
- Then - Three security profiles are created with conflicting policies
Steps
- securityprofile create –name secProfileTSP1 –file ./templates/secprofile.yml
- securityprofile create –name secProfileTSP2 –file ./templates/secprofile.yml
- securityprofile create –name secProfileTSP3 –file ./templates/secprofile.yml
- securityprofile test –name secProfileTSP1